Brute-Force Attacks occur when an attacker attempts to calculate every possible combination that could make up a password and test against your site to see if it is a correct password. This can be done either by using dictionary words or trying to guess the key created by key derivation functions to encrypt passwords into a secret value.
Attackers use a computer program or script, which automatically attempts all possible combinations to gain access. As computer hardware becomes faster and capable of doing more calculations per second, brute force attacks have become more popular as a means to obtain sensitive information stored in databases and other web hosting.
Table of Contents
Recognizing Brute-Force Attacks
Brute-force attacks are detectable by their volume, rather than the type. You’ll notice a large amount of failed login attempts in your web logs. You may also see the same account logging in over and over with different passwords and from multiple IP addresses.
Here is a list of logs to check:
Service Logs:
- /var/log/maillog or /var/log/mail.log – Email service logs
- /var/log/exim_mainlog – Exim logs
- /var/log/messages – FTP logs
- /var/log/auth.log or /var/log/secure – Contains user authorization information
cPanel/WHM Logs:
- /usr/local/cpanel/logs
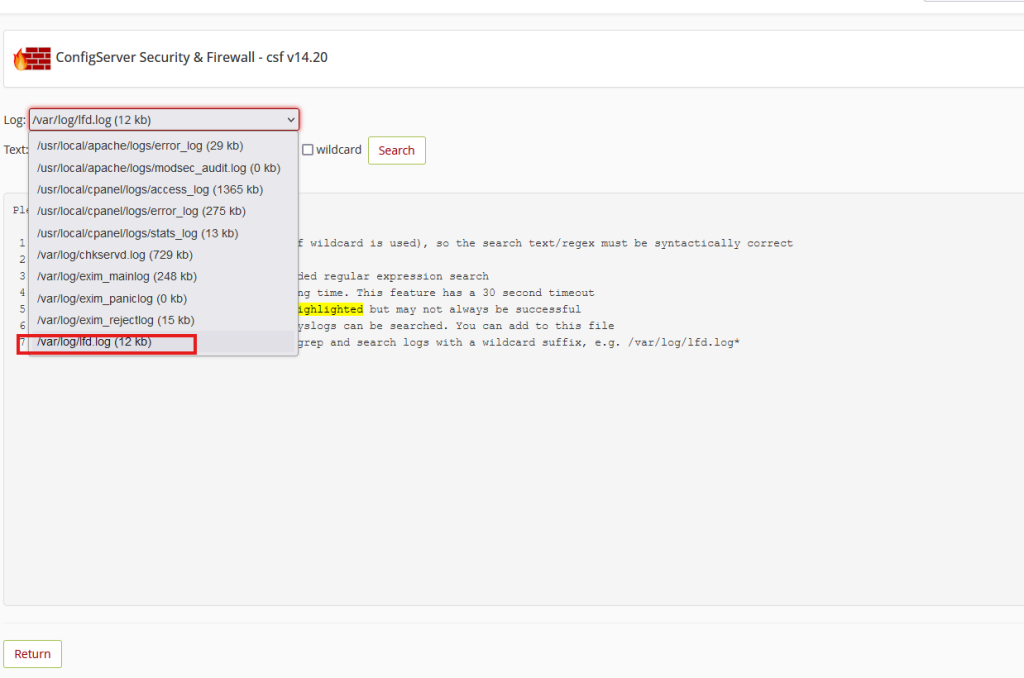
- /var/log/lfd.log
You can check these logs either by command line or within WHM under the ConfigServer Security & Firewall (CSF) home page. You can search (grep) system logs or watch (tail) system logs from here.
Key Characteristics of Brute-Force Attacks:
- Exhaustive Search: The attacker tries every possible combination of characters, starting from the simplest (e.g., “aaaa”) to the most complex until they find the correct one.
- Automated Tools: Attackers often use automated software tools to carry out attacks, which can rapidly generate and test thousands or even millions of password combinations.
- Time-Intensive: The effectiveness of a attack is heavily dependent on the length and complexity of the password or key. Stronger passwords (those that are longer and use a combination of letters, numbers, and special characters) take significantly longer to crack.
- Detection and Mitigation: Many systems have protections against attacks, such as account lockouts after a certain number of failed attempts, CAPTCHA challenges, or increasing delay times between login attempts.
Types of Brute-Force Attacks:
- Simple Brute-Force Attack: Testing all possible passwords without any optimization or prioritization.
- Dictionary Attack: A more refined brute-force approach where the attacker uses a predefined list of commonly used passwords (a dictionary) instead of trying all possible combinations.
- Hybrid Attack: Combines dictionary attacks with brute-force methods by altering known words with common variations (e.g., adding numbers or changing case).
- Reverse Brute-Force Attack: The attacker starts with a known password and attempts to find a matching username, typically targeting systems where the same password is used across multiple accounts.
Preventing Brute-Force Attacks:
- Strong Password Policies: Enforcing complex passwords that are difficult to guess or crack.
- Account Lockout Mechanisms: Temporarily locking accounts after a certain number of failed login attempts.
- Two-Factor Authentication (2FA): Adding an additional layer of security that requires something the user knows (password) and something the user has (like a smartphone or security token).
- Rate Limiting: Restricting the number of login attempts from a single IP address within a specific time frame.
Brute-force attacks can be powerful, but with proper security measures, they can be effectively mitigated.